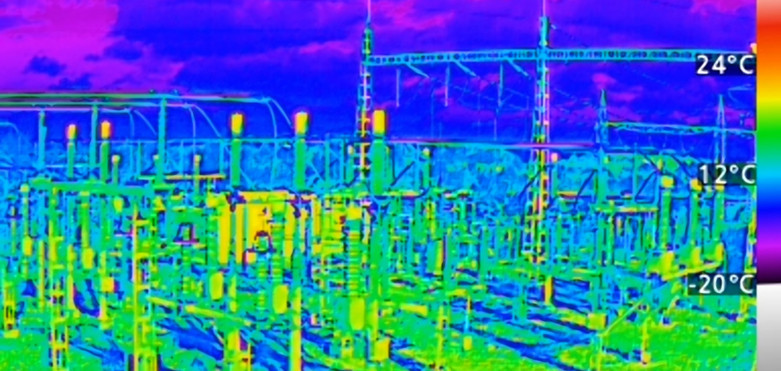
Temperature monitoring in hazardous areas can optimize operational efficiency
Across a wide range of industrial processes, temperature is an indicator of machine or system health. While rising temperatures can indicate the potential for overheating, lower temperatures can signal a pressure leak. As a result, the ability to effectively monitor system temperature is an important contributor to optimizing operational efficiency. Most seriously, rapidly rising temperature … Continued