The critical role of lifecycle management in maintaining strong cybersecurity
It there’s one thing the rise in highly-publicized data breaches has taught us it’s that cybersecurity should be a priority for every organization with a network. Threats from unauthorized and unwanted intrusion are real. And if you’re not vigilant in protecting your devices and systems, the results can be catastrophic—anything from loss of customer confidence to business closure.
As our world becomes more interconnected through the Internet of Things, every device and system on the network has the potential to become a breach point. Recognizing the criticality of the situation, many organizations are starting to proactively institute layered protection practices to secure their networks and everything attached to them. While these measures have proven effective, they represent only part of the story.
There’s another equally important, but often overlooked, action that organizations need to take to help shield their networks and critical data from threats and vulnerabilities: lifecycle management.
Without an effective way to manage the lifecycle of your physical assets it would be nearly impossible to meet the evolving cybersecurity challenges to your digital assets. The two tasks are intricately linked.
Let me explain. Lifecycle management encompasses two types of lifetimes associated with devices. The longer of the two is a device’s functional lifetime, meaning how long you can realistically expect it to operate and function appropriately. The second is its economic lifecycle, meaning how long until the device starts costing more to maintain than adopting new, more efficient technology.
Secure systems depend on proactive maintenance
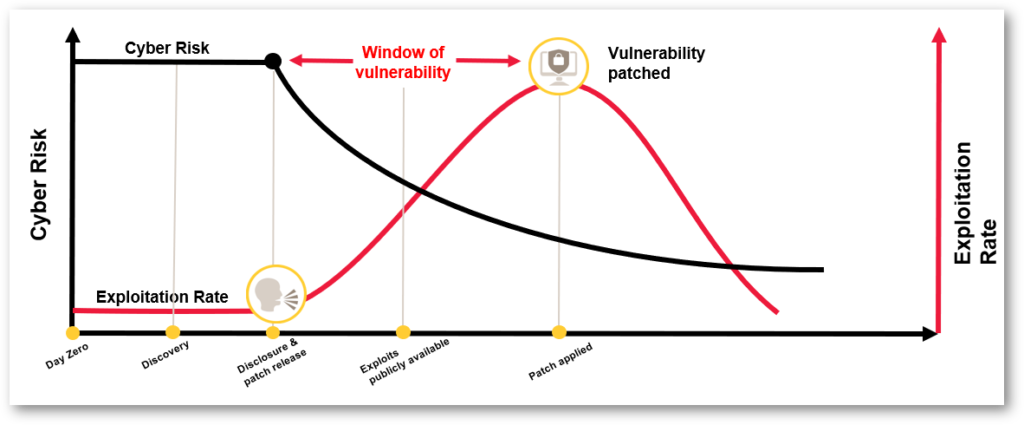
In looking at a device’s lifecycle, it’s easy to see that proactive maintenance is the best way to ensure a more stable and secure system. This is especially true in today’s ecosystem of connected and interdependent devices and solutions. That’s why responsible manufacturers regularly release firmware updates and security patches to address vulnerabilities, fix bugs, and resolve other issues that may affect performance over time.
Because the threat landscape continues to evolve, it’s inevitable that virtually all software-based technology will need to be patched at some point to prevent attackers from exploiting known vulnerabilities and undermining existing protections. Security devices like network cameras, network audio, video intercoms, entry control systems and the like are no exception. That’s why it’s imperative that network administrators stay on top of a broad spectrum of developing threats and follow the latest cybersecurity best practices to address them. Regular updating and patching should also extend to the video management system (VMS) that controls the overall system as well as the operating system on which it runs.
Despite the critical need to update software when new firmware is made available, the unfortunate reality is that many organizations fail to do so. The most common excuse is the time and effort involved in updating each separate device connected to the network. This problem is compounded by the fact that many organizations simply don’t know what technologies are deployed on their network.
Hope is not a plan
Securing an enterprise network starts with a solid understanding and comprehensive history of the devices connected to your network. That history must include documentation about every device because any overlooked device could easily become an entry point for attackers.
Older technologies represent the greatest risk to an organization, especially from a cybersecurity perspective. Of course, updates and patches are the best way to improve cybersecurity, but many older technologies have little to no update capabilities. In fact, they may no longer be supported by the manufacturer. Unpatched technology leaves networks vulnerable to cyberattack. However, following lifecycle management best practices—such as knowing where risk areas lie and keeping current on how those areas might be exploited—helps you ensure your business stays secure.
Regardless of their function, all technologies eventually reach end of life, whether through functional breakdown or obsolescence. You can hope your devices run forever, but hope is not a plan. A structured lifecycle management program helps you avoid those unwelcomed surprises like needing to suddenly replace a major system component. With greater oversight, you can plan out a systematic replacement schedule and budget for a predictable percentage of devices each year, including major components approaching their end of useful life.
Keeping pace with threats
Lifecycle management goes hand in hand with using the most appropriate and advanced technologies to minimize security threats and vulnerabilities. This approach is especially important for critical technologies like security systems. If a network surveillance camera goes down the consequence could be dire.
While an IP camera typically has a functional lifetime of 10 to 15 years, its actual lifespan may be shorter due to rapid changes in the cybersecurity landscape. It may reach a point where the manufacturer simply can’t update it any more to combat the latest cyberthreats.
Instituting a lifecycle management program helps you stay focused on the critical technology in your environment and avoid the negative costs associated with cyberbreaches. It allows your organization to identify devices that are nearing end of life and more susceptible to risk because they won’t be receiving future firmware updates. Some of these technologies may be running on outdated operating systems that are incapable of being updated or secured. In either case, you’ll know when these devices must be replaced with newer solutions that the manufacturer currently supports.
Streamlining lifecycle management
Effective lifecycle management can be a daunting task for organizations and network administrators. Thankfully there are device management software solutions that can automate the process, alleviating this costly and time-consuming burden.
They can quickly assemble a full real-time inventory of all the cameras, encoders, access control, audio, and other devices connected to your network. This makes it easier to implement consistent lifecycle management policies and practices across all your devices and securely manage all major installation, deployment, configuration, security, and maintenance tasks.
How lifecycle management works
When device management software discovers a device on your network it also captures key information about it:
- Model number
- IP address
- MAC address
- Current firmware loaded on the device
- Certificate status
Once it collects that data for every device, it imports it into a subprogram that displays the information to those who need to use it. Integrators, installers, and system administrators can use this highly detailed look at the network ecosystem to efficiently perform a variety of maintenance tasks. This includes managing user privilege levels, password changes, firmware updates, and configuration modifications—all critical parts of lifecycle management and cybersecurity best practices.
One of the best benefits of using device management software is that you can push out system changes, firmware updates, and new HTTPS and IEEE 802.1x security certificates to hundreds of devices simultaneously, rather than individually. It’s also a highly efficient and easy way to create or reconfigure security settings and apply them across your entire network of devices, ensuring that they comply with your organization’s most current security policies and practices.
For instance, when your administrator receives notice of expiring security certificates, the device management software can automatically push new certificates to all the appropriate devices. In the case of firmware upgrades, the software automatically verifies that the devices are running the latest and most secure version.
This function can save your system administrators a lot of time and stress when it comes to managing cybersecurity risk because they can address new vulnerabilities more quickly and thereby limit exposure. Ordinarily, when a vulnerability is announced, people tend to panic and scramble to figure out whether the devices they have on their network may be at risk. Device management software eliminates that sense of panic. It spells out exactly where you stand on the cybersecurity front and what steps need to be taken to protect your technology—whether it’s downloading a patch, updating a certificate, upgrading firmware, etc. And that leads to a more stable and secure system overall.
Maintaining consistent lifecycle management and cybersecurity policies
As we all know, a network is only as secure as the devices connected to it, which is why IT departments expect strict adherence to cybersecurity protocols and practices. Whether you’re managing physical security technology or other systems on the network, you should be having ongoing discussions with IT’s security team to make sure your devices comply with their established lifecycle management and cyber policies and procedures. For instance, you might want to ask if IT has policies around:
- Changing factory default passwords before devices go live
- Password strength and how often users need to change their passwords
- Turning off unused services to reduce surface area for potential attacks
- How frequently devices on the network are scanned for vulnerabilities
- Assessing risk levels when manufacturers post known exploitations
- How often devices get upgraded with new firmware
- Meeting compliance regulations like HIPPA, PCI, and NDAA
The nature of our interconnected world makes cybersecurity everyone’s concern. State-of-the-art, cyber-hardened devices are a good starting point for protecting networks. However, to be most effective, these technologies must be augmented by strong lifecycle management practices. Using device management tools to automate your lifecycle management processes can provide your organizations with the real-time insight into the state of your ecosystem. You’ll be able to see in an instance that devices are up to date with the latest patches, firmware updates, and certificates from manufacturers or flagged for removal when no longer supportable. With timely oversight and consistent policies and procedure in place, you’ll be able to anticipate when devices are reaching end-of-life, determine if malware could potentially infect your devices, and resolve a host of other vulnerability issues before they compromise your network. And that’s what proactive ecosystem security is all about.
Want to see AXIS Device Manager at work?
Ryan Zatolokin is a Senior Technologist for Axis Communications. He can be reached at Ryan.Zatolokin@axis.com.