-
North and Central America
Can't find your location? Visit our global site in English.
-
South America
Can't find your location? Visit our global site in English.
- Asia
-
Oceania
Can't find your location? Visit our global site in English.
-
Europe
- Austria - Deutsch
- Belgium - English Français
- Czech Republic - Česky
- Finland - Suomalainen
- France - Français
- Germany - Deutsch
- Italy - Italiano
- Netherlands - Nederlands
- Poland - Polski
- Portugal - Português
- Romania - Română
- Spain - Español
- Switzerland - Deutsch Français Italiano
- Sweden - Svenska
- Turkey - Türkçe
- United Kingdom - English
- Kazakhstan - Русский
- Africa and Middle East

Latest news: Three ways XProtect users can utilize AI-powered analytics and metadata for free
Work smart! Discover how to accurately respond to real-time events, accelerate forensic search and make data-driven decisions. Everything is optimized for and united in XProtect Management and Smart Clients by AXIS Optimizer.
Find, install and maintain plugins
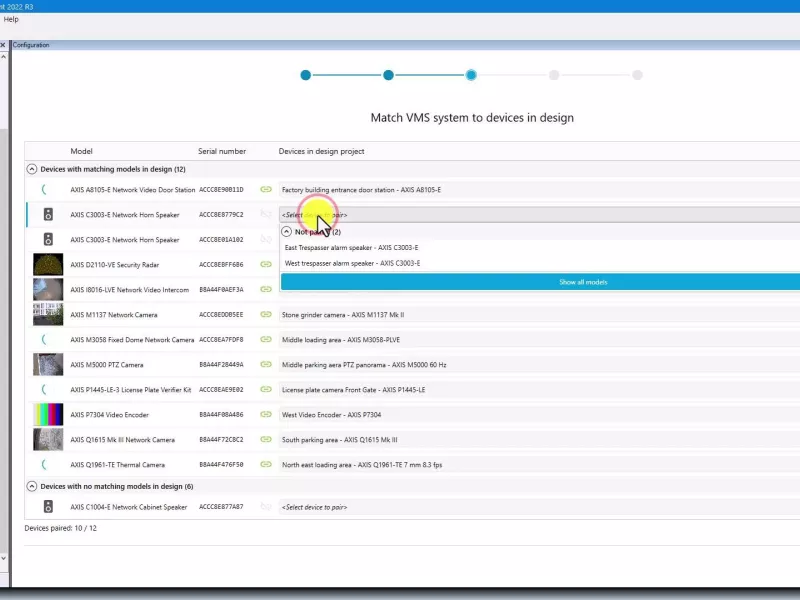
Available a free one-time installer, AXIS Optimizer is an integrations suite for Axis-Milestone systems. Admin roles install all needed device plugins and integrations — one time — and update everything automatically. This offers significant time savings as there’s no need to search for, download, install, configure, update and maintain multitudes of separate device plugins and integrations.
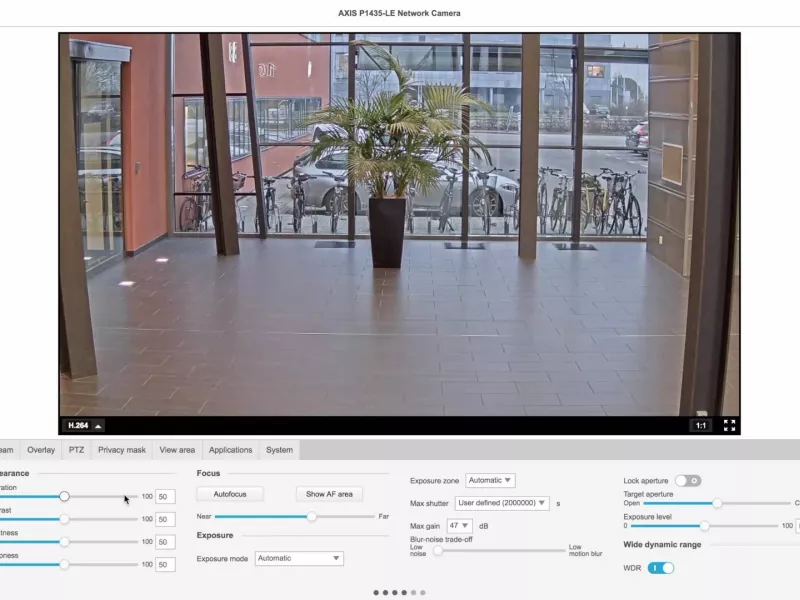
Easily access device settings
Gaining easy access to Axis device settings delivers time savings and ensure efficient outcomes. Admin and operator roles can directly access any Axis device's settings directly in XProtect. Without AXIS Optimizer, users need to log into the web GUI of each device to change its different settings. The larger the system, the more devices connected to it, the more time and effort is required to configure and tweak the connected devices.
Examples of Device settings
Direct access
Gain direct access to all settings for Axis devices within XProtect. For instance, to easily adjust settings and configure your devices.
Manage applications
Easily adjust and configure analytic applications within XProtect, such as video motion detection, loitering, and AXIS Object Analytics, and copy settings to other devices.
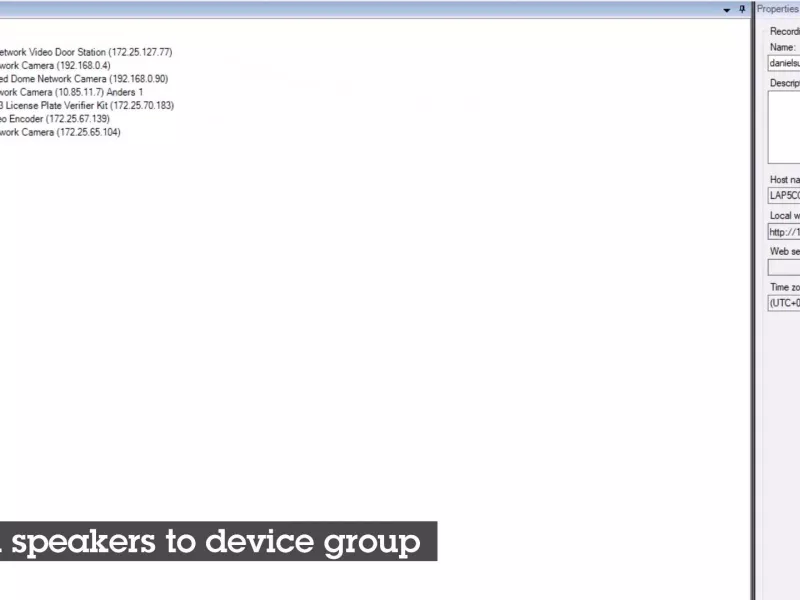
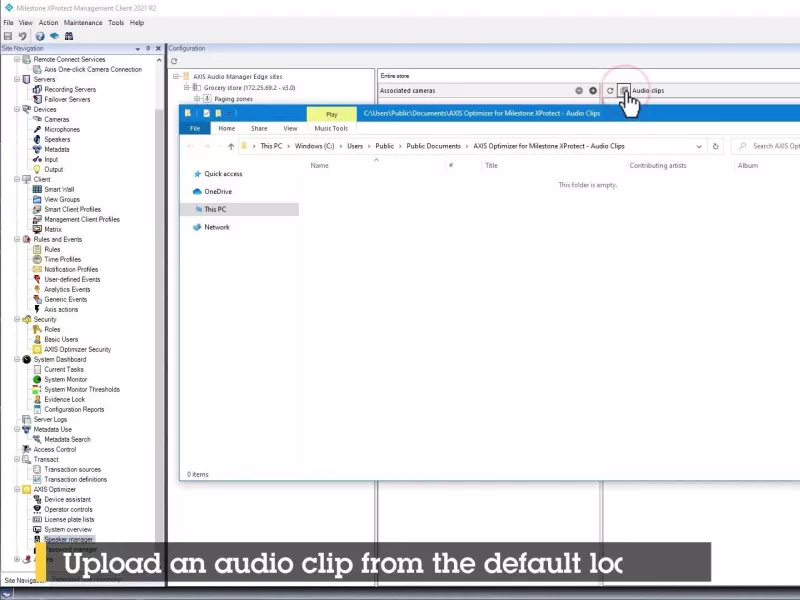
Manage speakers
Integrate the full capabilities of Axis audio devices into XProtect to access professional audio capabilities, including zone management, volume control, and content scheduling.

Set autotracking
Select objects and set up trigger areas to enable a device to automatically track moving objects.
Easily access extended device features
Many Axis devices have device-specific features built-in which deliver full capabilities. Without AXIS Optimizer for XProtect, users must access each device at sites to access these extended features. Operators typically don’t have privileges for this so they would need approval from their system administrator — or the administrator needs to do this work themself. Depending on site and device connectivity, this often also requires travel to each location. Again, the more devices connected to the system, the more time and effort is required to manage extended device features.
Examples of Extended device features
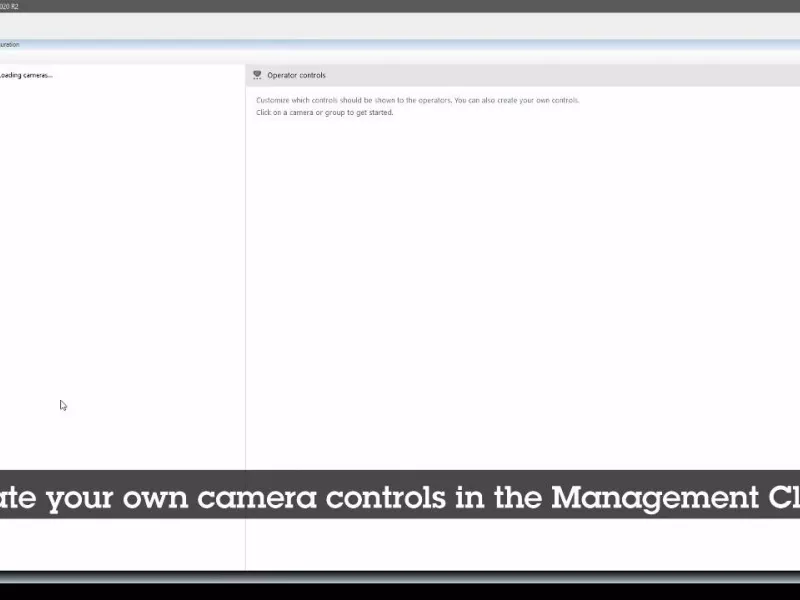
Set up operator controls
Access an Axis camera’s specific features in XProtect Smart Client, including both preinstalled and custom controls.
Set focus area for PTZ cameras
Set up focus recall for pan/ tilt/zoom cameras and ensure the camera recalls the focus position for any given predefined area.
Set autofocus for cameras
Ensure the camera’s lens remains focused on the area or object of interest when the view changes.
Sharp images in rainy weather
Turn on/off speed dry in dome cameras and wipers in positioning cameras to ensure sharp images are delivered under rainy weather or wet condition.
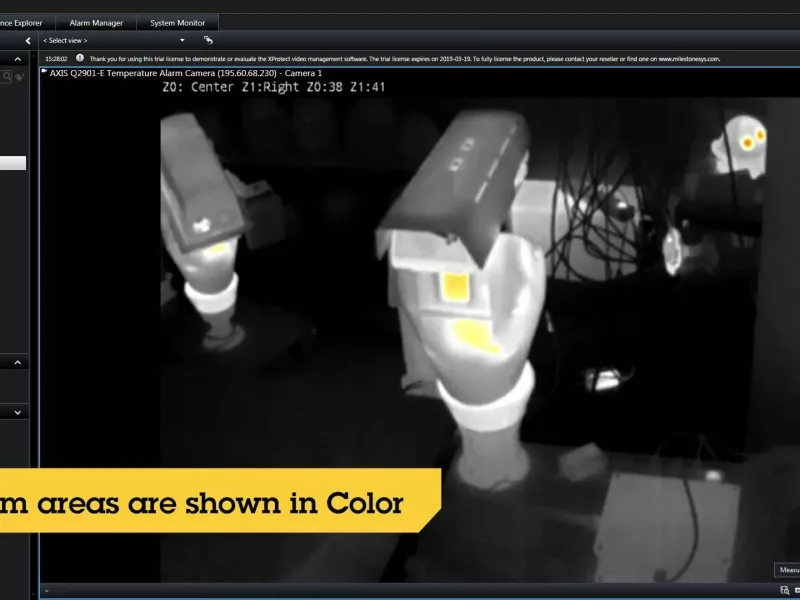
Measure spot temperatures
Enable one-click, real-time measurement of the temperature of any particular area or object in a scene.
Manage dewarped video
Run client-side dewarping of video captured with wide-angle cameras, and ensure clear, natural views with improved usability, coverage, and accuracy.
Apply security controls and manage video management systems

A one-size-fits-all, all-in-one feature that could make any security system and site 100% cybersecure. As appealing as those words sounds, no such feature exists — or is likely to anytime soon. While there is no quick fix, there are effective means to apply security controls inorder to mitigate risks. AXIS Optimizer helps administrators save time and effort applying these by managing user privileges to the suite as well as efficiently manage all Axis devices connected on all sites in and Axis-Milestone local or distributed systems.
Examples of Security controls
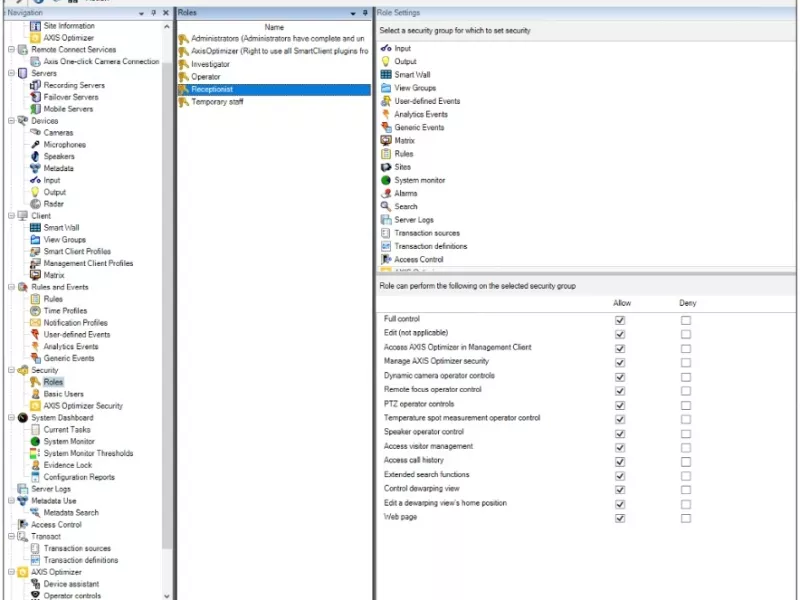
Manage user privileges for AXIS Optimizer
Configure which AXIS Optimizer capabilities an operator has access to through AXIS Optimizer's built-in security role settings.
Auto-upgrade all connected Smart Client machines remotely
Remotely perform upgrades of AXIS Optimizer on all connected Smart Client machines without operator interaction, ensuring everything is always up to date.
Manage Axis devices on your sites
Use AXIS Device Manager to manage and upgrade Axis devices and ensure you always have the latest AXIS OS capabilities.
Import device configurations
Import and configure settings from AXIS Site Designer and ensure a controlled system design.
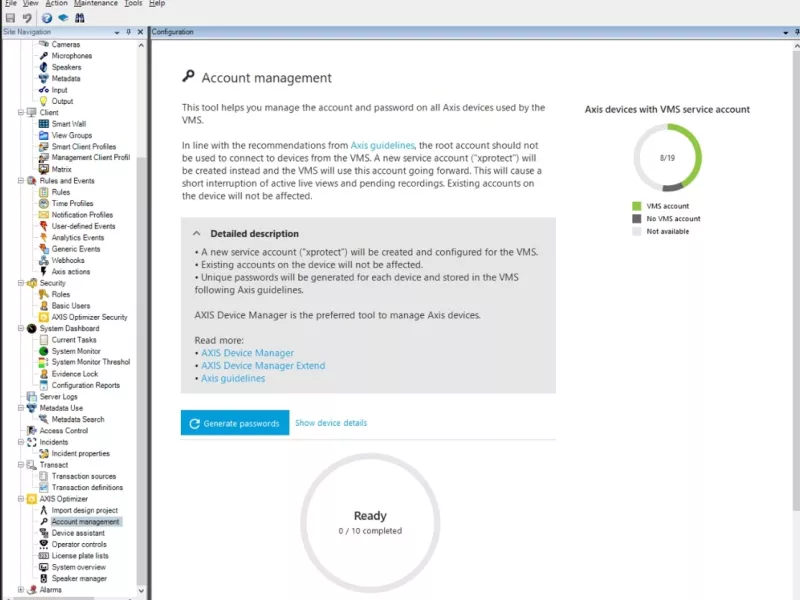
Account and password management
Manage accounts and passwords for Axis devices and create a XProtect service account with unique 16-character passwords for each device.
Manage events for Axis devices
Use a dedicated control panel as a centralized hub to manage Axis device events. Get a full status overview and manage and troubleshoot events directly in XProtect.
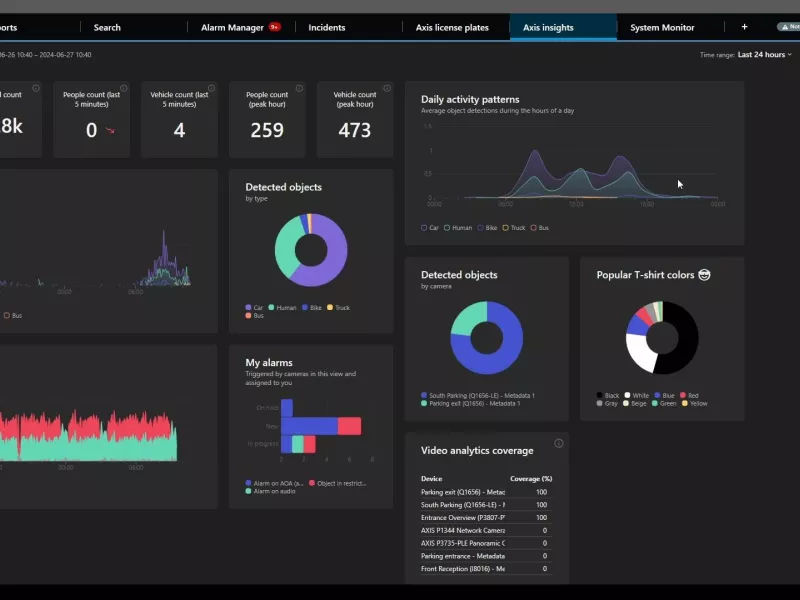
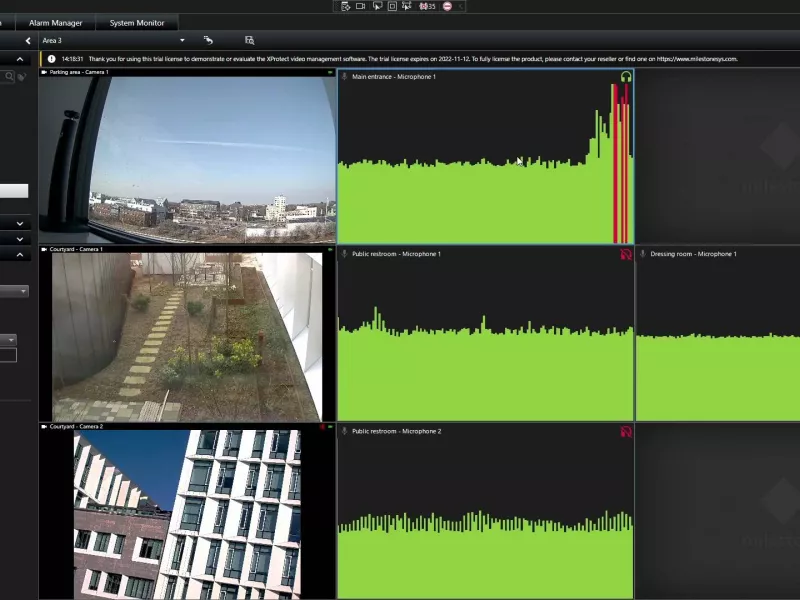
Use metadata dashboards
Use real-time data produced from connected Axis devices to gain actionable insights in the form of graphs showing statistics, trends, and anomalies.
Perform automated actions
Operators must monitor and deal with real-time events efficiently, accurately and repeatably. Given today’s ever more connected and intelligent devices, the sheer amount of events increases. Meanwhile, properly managing them involves performing manual tasks, which heightens risks for mistakes or delays. If an event is missed, you risk unwanted situations such as leaving visitors waiting at a door.
Examples of Automation
Automatically play audio clips
Set up custom rules and use Axis cameras with AXIS Audio Manager to automatically play an audio clip or broadcast a live message from a speaker when a camera detects motion.
Automatically dry all cameras
Set up custom rules to automatically dry multiple dome cameras with speed dry and positioning cameras with built-in wipers.
Autofocus for multiple cameras
Ensure the camera’s lens remains focused on the area or object of interest when the view changes.
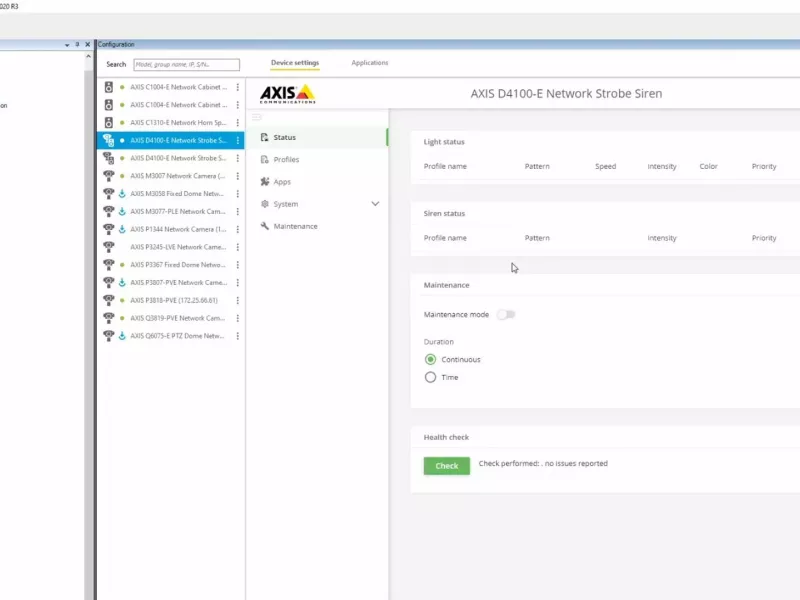
Auto-activate strobe sirens
Set up custom rules to automatically trigger strobe sirens to activate audio and visual alerts when a camera detects motion.
Automation of privacy masks
Create a rule to turn on/off privacy masks when an analytics event occurs.
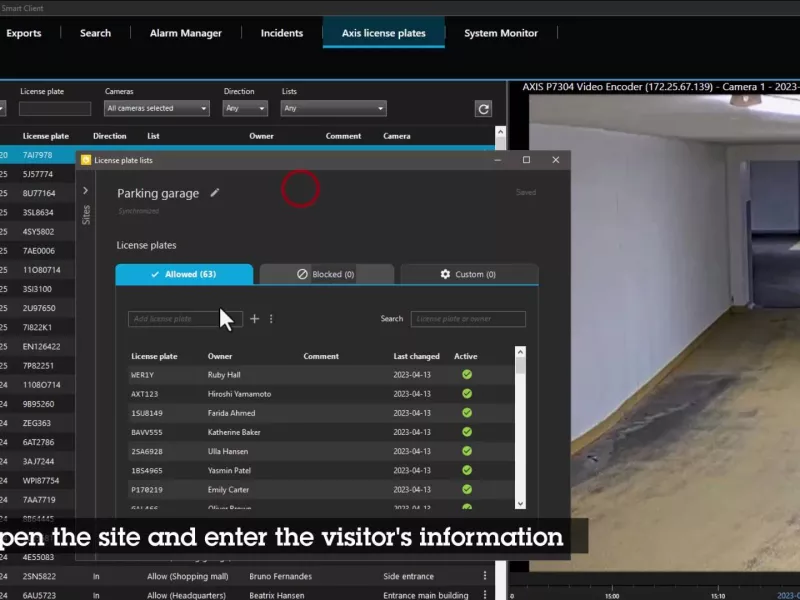
Automatic vehicle access
Create automated actions to grant vehicle access upon entry and exit. Centrally manage license plate lists as credentials and search for and export license plate entries in event logs.
Respond to real-time events

Responding to real-time events typically requires operators to perform actions manually based on alerts. Such work is prone to human error and takes time — which is precious when dealing with real-time incidents. If an operator doesn’t respond quickly and accurately to a potential threat, the incident can escalate. Traditionally, an operator needs to access multiple device and VMS rules and settings to manage events. Axis offers a broad portfolio of network devices that enable operators to respond to incidents. With AXIS Optimizer, admin roles are assured accurate, timely actions can be taken.
Examples of Real-time events

Audio responses through speakers
Use audio to respond through speakers to real-time events. Push-to talk, broadcast pre-recorded messages, manage audio zones and clips, schedule content adapt volume and more.
Respond via audio only
Use audio to respond to events in areas where only audio detection is allowed.
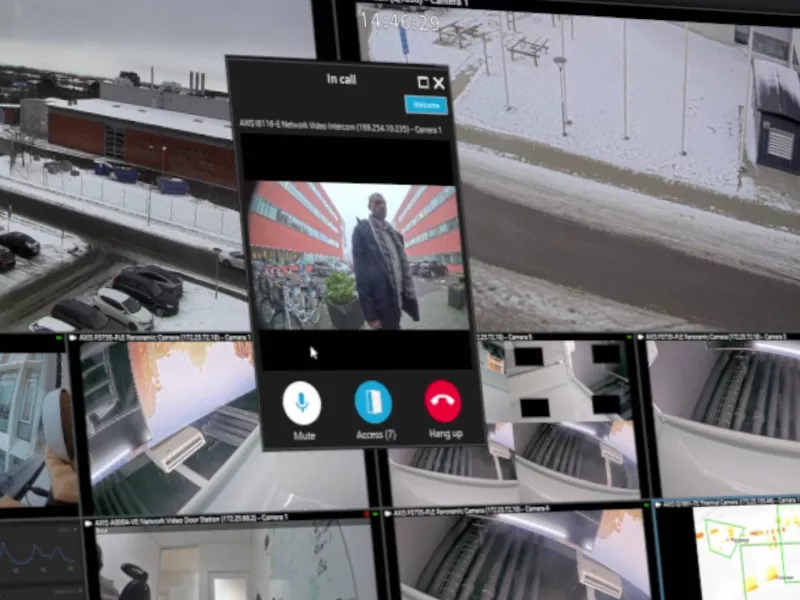
Call routing
Prioritize and route incoming intercom and SIP phone calls without disturbing the operator.
Perform pre-set actions
Press a preset action button on the intercom's screen to execute specific actions, such as open multiple doors or turn on lighting.
Use metadata to trigger actions
Use metadata to trigger actions based on motion detection, line crossing, objects in area, occupancy and more to efficiently manage real-time situations
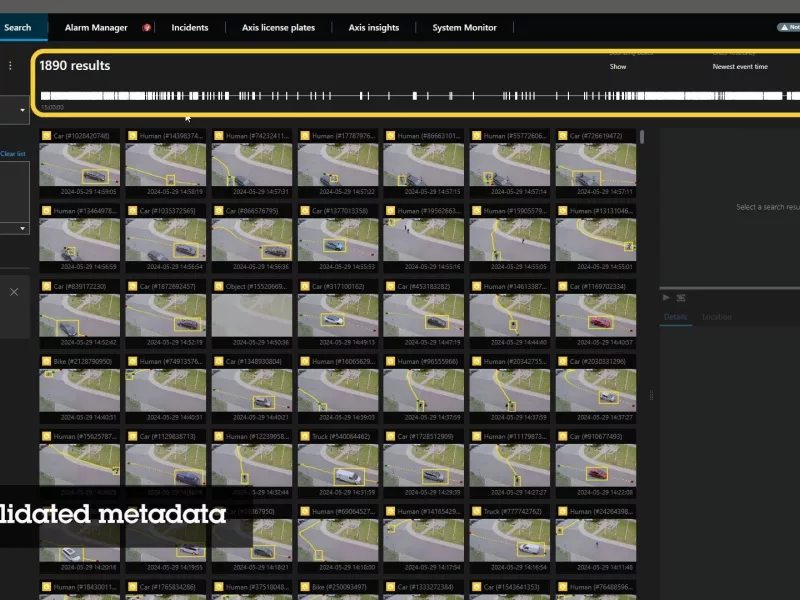
Accelerate forensic search investigations

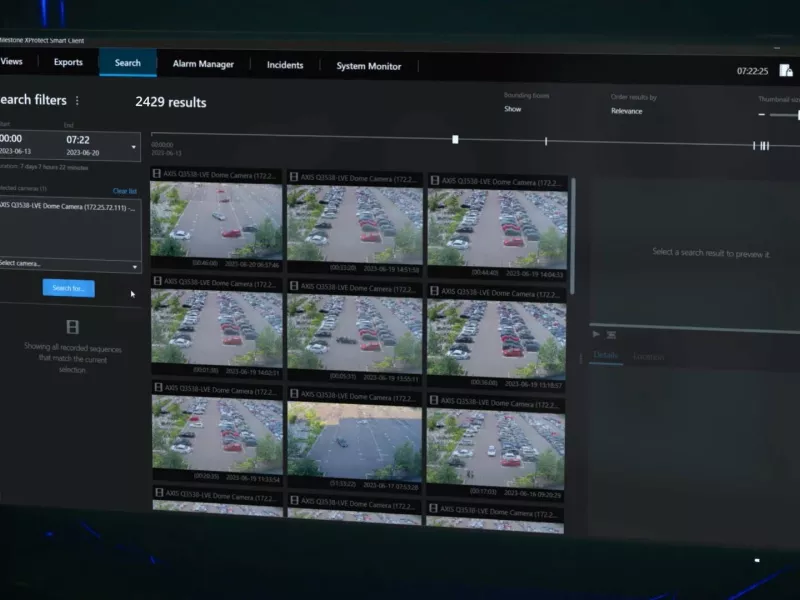
The vast majority of forensic investigations involve video evidence. Operator and investigator roles are often not certain of what or whom they are looking for, where or when an incident took place, how objects or people moved in the location of the incident. Plus, the sheer amount of video and data from just one camera mounted at one location over a day, week or even longer is extensive — the greater number of cameras, the more there is to review. Natively searching through hours of footage to find a specific person or object can be time-consuming, error-prone and tedious. AXIS Optimizer saves you time to turn raw data into evidence.
Examples of Forensic search
Objects
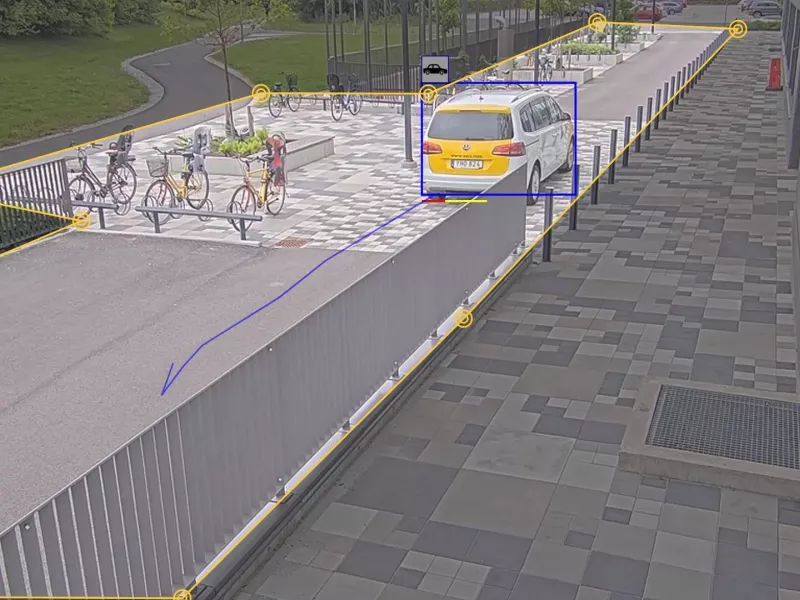
Search for, recover, and share video evidence about objects (people, and vehicles) — no analytics servers required.
Vehicles
Search for, recover, and share video evidence derived from Axis or third-party license plate recognition applications — no analytics servers required.

Freight containers
Search for, recover, and share video evidence from third-party analytics about freight containers — no analytics servers required.
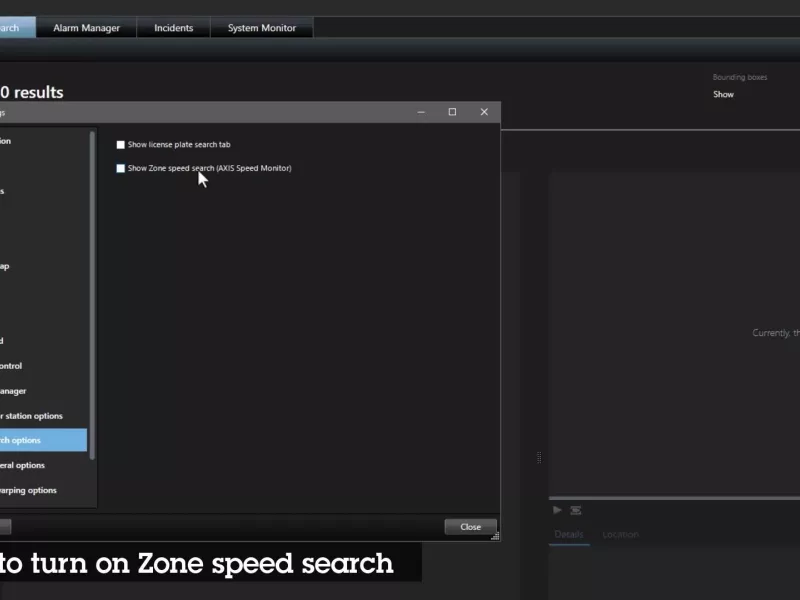
Zone speed infractions
Search for, recover, and share evidence from Axis radars about zone speed infractions — no analytics servers required.
Customize metadata and forensic search
Control metadata and forensic search capabilities, and turn on and off settings for event data, analytics data, consolidated metadata, and forensic search filters for each Axis device.
Manage access control
Axis Secure Entry for XProtect unites access control and video surveillance in XProtect. No more jumping between interfaces to manage door entry, door monitoring, door assistance, and door entry investigation events. One familiar, intuitive interface for operators to view video, handle alarms, receive intercom calls, run investigations, securely share evidence, and more. So it's easy to figure out what’s happening at the door and manage workflows.