-
North and Central America
Can't find your location? Visit our global site in English.
-
South America
Can't find your location? Visit our global site in English.
- Asia
-
Oceania
Can't find your location? Visit our global site in English.
-
Europe
- Austria - Deutsch
- Belgium - English Français
- Czech Republic - Česky
- Finland - Suomalainen
- France - Français
- Germany - Deutsch
- Italy - Italiano
- Netherlands - Nederlands
- Poland - Polski
- Portugal - Português
- Romania - Română
- Spain - Español
- Switzerland - Deutsch Français Italiano
- Sweden - Svenska
- Turkey - Türkçe
- United Kingdom - English
- Kazakhstan - Русский
- Africa and Middle East
A shared responsibility
We want to make it easier for you to put safeguards in place, so you can use our offerings in as secure a manner as possible. Mitigating the risks of cyberthreats is a shared responsibility.
Why cybersecurity is important?
Protecting networked products and software services from cyberthreats is key to securing the data and systems on your network.
What are the threats?
Threats to your system can be anything that can compromise or cause harm to your IT assets or resources. Common threats include unauthorized access, sabotage, and exploitation of vulnerabilities.
A compromised system can mean the loss of confidentiality and integrity of your data, or data can be unavailable when you need it.
Helping you do your part
Find below a range of resources that can help you to safeguard your system. And learn how we support cybersecurity – and you – throughout the lifecycle of an Axis product.
QUICK LINKS
Q&As
Find answers to common questions.
Resources
At a glance, access a host of cybersecurity resources, including hardening guides and policy documents.
HIGHLIGHTS
Securing better together
Learn about the cybersecurity measures Axis supports throughout the lifecycle of an Axis product.

Software development
Learn how cybersecurity is an integral part of software development at Axis.

Edge Vault cybersecurity platform
The hardware-based cybersecurity platform safeguards the integrity of Axis devices and enables the execution of secure operations based on cryptographic keys.

AXIS OS platform
Learn how AXIS OS, the operating system that powers most Axis devices, supports new security features and patches throughout a product's lifetime.

Supporting enterprise IT
Axis devices integrate seamlessly into enterprise IT infrastructure. Learn, for instance, how Axis supports zero-trust networks.

Device security management
Axis device management software programs make it easy for you to protect and manage your devices throughout their lifetime.

Vulnerability management
Axis is a CVE Numbering Authority, so we follow best practices in managing and responding to discovered vulnerabilities in our offering.
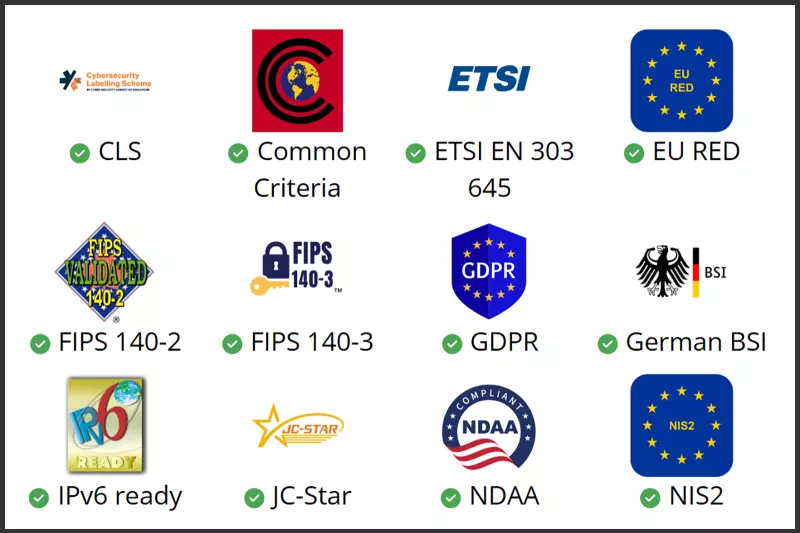
Cybersecurity compliance
Axis, as a company, and our products support compliance with various cybersecurity-related regulations and standards.

News
See cybersecurity-related news from Axis.

Axis cybersecurity e-brochure
The e-brochure covers topics such as cyberthreats, procurement considerations, the Axis device lifecycle approach, and compliance.